Welcome to the blog series:
Exploring Microsoft Azure Landing Zone Best Practices.
In this series, we will dive deep into the concept of the Azure Landing Zone and explore the best practices that organizations can follow to design, implement, and manage their Azure estate effectively.
Whether you are new to Azure or already have an existing Azure environment, this series will provide valuable insights and guidance to optimize your cloud journey using Azure Landing Zone.
Chapter 2: Planning Your Azure Landing Zone: Key Considerations for Success
- Introduction: Importance of proper planning
- Assessing organizational requirements and goals
- Understanding Azure Resource Hierarchy and Role-Based Access Control (RBAC)
- Defining deployment regions and networking considerations
- Azure Policies, Blueprints, and Governance frameworks
Introduction: The importance of proper planning
When it comes to building a solid foundation for your Azure infrastructure, proper planning is crucial. Chapter 2 of our blog series will delve into the essential aspects of planning your Azure Landing Zone. By thoroughly assessing organizational requirements and goals, understanding the Azure Resource Hierarchy and role-based access control (RBAC), defining deployment regions, considering networking options, and implementing Azure policies, blueprints, and governance frameworks, you’ll be well-prepared to design a resilient and scalable Azure environment.
Assessing Organizational Requirements and Goals
Effective planning begins with understanding your organization’s unique needs and goals. Start by assessing your current IT infrastructure, identifying pain points, and determining the specific objectives you aim to achieve with Azure. Consider factors such as scalability, security, compliance, cost optimization, and future growth. Engage with stakeholders, collaborate across teams, and document your findings to define a clear vision of what you want to accomplish.
Understanding Azure Resource Hierarchy
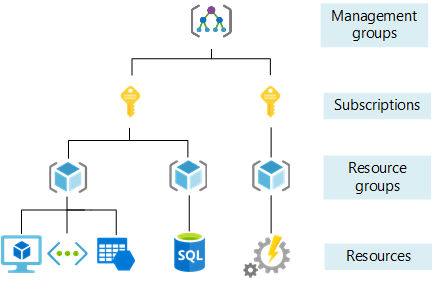
The Azure Resource Hierarchy provides a logical structure for organizing and managing resources within your Azure environment.
It consists of three levels:
1. Management Groups: Use management groups to group subscriptions that share common attributes, policies, or governance requirements. They provide hierarchical governance and make it easier to apply policies at scale.
2. Subscriptions: Subscriptions are containers for organizing and isolating resources. They enable you to manage access control, billing, and resource usage for different business units, projects, or environments.
3. Resource Groups: Resource groups are logical containers within a subscription that enable you to manage and scope access control, apply policies, and track costs for specific sets of resources.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a fundamental component of the Azure Resource Hierarchy, enabling you to grant appropriate access permissions to users within your Azure environment. RBAC allows you to assign roles to users, groups, or service principals to control what actions they can perform on resources within a subscription or resource group.
Azure provides several built-in roles with different levels of permissions, such as Owner, Contributor, Reader, and User Access Administrator. These roles are based on common job functions and provide a predefined set of permissions. However, Azure also allows you to create custom roles that align with your organization’s specific needs.
RBAC follows the principle of least privilege, which means granting users only the permissions necessary to perform their tasks, thereby reducing the risk of unauthorized actions. By assigning roles at different levels of the Resource Hierarchy, you can control access to resources based on business requirements and secure your environment effectively.
RBAC can be implemented by assigning roles directly to users and groups, or by using Azure AD for identity and access management. Azure AD integration allows you to use your existing on-premises Active Directory configurations, enabling seamless authentication and access control across both on-premises and Azure resources.
By effectively utilizing the Resource Hierarchy and RBAC in Azure, you can achieve better organization, governance, and security for your Azure resources. It allows for fine-grained access control and ensures that users have the appropriate level of permissions to perform their tasks. By organizing resources into logical containers and applying RBAC, you can easily manage permissions, track costs, and enforce policies throughout your Azure environment.
Defining Deployment Regions and Networking Considerations
Selecting the appropriate deployment regions and networking options is critical for optimizing performance, ensuring redundancy, and complying with data residency requirements. Consider the following:
1. Deployment Regions: Choose the Azure regions where your resources will be deployed. Factors such as latency, compliance regulations, and customer proximity may impact this decision. Consult the Azure Regional Services List to determine which services are available in each region.
2. Networking Considerations: Determine how you will create and connect networks within your Azure Landing Zone. Consider using Azure Virtual Networks (VNets) to isolate and secure your resources. Define appropriate subnet size allocations and network security group (NSG) rules to control traffic. Explore connectivity options such as VPN gateways or Azure ExpressRoute for secure communication between on-premises networks and Azure.
Azure Policies, Blueprints, and Governance Frameworks
Governance frameworks refers to a set of practices, policies, and guidelines that govern the use of Azure resources within an organization. It provides a structure for decision-making, risk management, and compliance. Implementing a governance framework ensures that the Azure environment aligns with organizational goals, while also maintaining security, compliance, and cost optimization.
Azure Policies enable you to enforce compliance requirements and implement best practices across your Azure environment, thus enforcing a particular governance framework. By defining policies, you can ensure that resources adhere to specific configurations, security standards, or naming conventions. Continuously monitor and enforce these policies to maintain a well-governed infrastructure.
Azure Blueprints provide a declarative way to orchestrate the deployment of Azure artifacts such as resource groups, policies, templates, and role assignments. Use Azure Blueprints to automate and standardize the creation of your Azure Landing Zone, ensuring consistent deployments across subscriptions.
Governance frameworks, such as the Azure Well-Architected Framework, can guide you through the process of organizing resources, implementing best practices, and ensuring compliance. These frameworks help establish a robust governance model tailored to your organization’s specific requirements, ensuring efficient resource management, and minimizing security risks.
An example of a governance framework for an Azure Landing Zone may include policies which can be defined in the following structure:
1. Resource Naming and Tagging Policy:
Implement a policy that enforces a standardized naming convention for Azure resources. This ensures consistency and makes it easier to identify and manage resources across the organization. In addition to naming, enforce the use of necessary tags for each resource to provide meaningful metadata for better asset tracking, cost allocation, and compliance monitoring.
2. Security and Compliance Policy:
Define security requirements and implement policies that ensure the confidentiality, integrity, and availability of Azure resources and data. This may include enforcing the use of security controls like network security groups (NSGs), firewalls, encryption, multi-factor authentication (MFA), and Azure Security Center for threat intelligence and monitoring. Implement compliance standards such as ISO 27001, GDPR, HIPAA, or industry-specific regulations relevant to your organization.
3. Cost Management Policy:
Establish policies and practices to optimize and control Azure costs. This may involve implementing Azure Cost Management and Azure Advisor to analyze usage patterns, identify cost-saving opportunities, and implement resource optimization strategies. Set budgets, implement cost allocation tagging, and regularly review and optimize spending to ensure cost efficiency.
4. Data Residency and Sovereignty Policy:
Define policies that adhere to geographical and legal requirements regarding data residency and sovereignty. Determine the Azure regions where data can be stored and processed based on compliance regulations and customer preferences. Implement mechanisms to monitor and control data locality to ensure compliance with relevant regulations.
5. Change Management and Approval Process:
Establish a change management process that governs the creation, modification, and deletion of Azure resources. Implement an approval workflow with appropriate authorization tiers to ensure that changes are properly reviewed and approved before implementation. This helps to mitigate risks and prevent unauthorized or uncontrolled changes that may impact the stability and security of the Azure environment.
6. Monitoring and Alerting Policy:
Define policies and practices for comprehensive monitoring and alerting in the Azure environment. Implement Azure Monitor to gain insights into performance, health, and availability of resources. Set up alerts for critical events or breaches of predefined thresholds to proactively detect and respond to issues before they impact services.
7. Documentation and Training Policy:
Ensure that documentation is maintained and up-to-date, including architectural diagrams, standard operating procedures (SOPs), and configuration management records. Implement a training program to ensure that Azure users and administrators are knowledgeable about the governance framework, policies, and best practices to maintain consistent standards across the organization.
By implementing a comprehensive governance framework, organizations can maintain control, security, and compliance while efficiently managing Azure resources. The framework provides a structure for decision-making, mitigating risks, ensuring consistency, and optimizing resource usage. It helps to align the Azure Landing Zone with organizational goals, regulatory requirements, and industry best practices.
Azure Blueprints
How then would we start to build out an Azure Blueprint to enforce such a framework in the real world? Azure Blueprints can be deployed using the Azure Portal, PowerShell or the RestAPI to achieve this.
Below is a sample of the artifact structure, which can consist of Role Assignments, ARM Templates, Resource Groups or Policies associated with a Blueprint:
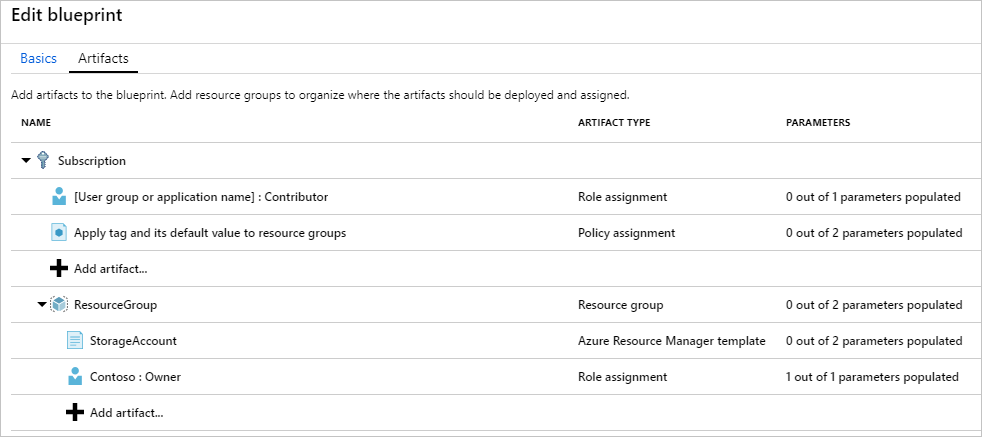
Source, Define and assign a blueprint in the portal
Azure Blueprint Structure
Let’s dive into a more detailed example of an Azure blueprint for enforcing a governance framework within an Azure Landing Zone.
Below are the sets of criteria we need in order to define the blueprint artifacts:
1. Blueprint Name: Governance Blueprint for Azure My Landing Zone (You can use up to 48 letters and numbers, but no spaces or special characters.)
2. Blueprint Description: This blueprint establishes a highly secure and compliant Azure Landing Zone by enforcing a set of policies, resource configurations, access control settings, and monitoring capabilities.
3. Policies:
– Require Azure Policy compliance: Enforce the use of Azure Policy to ensure resource compliance. This includes policies to enforce tagging standards, network security controls, encryption requirements, and regulatory compliance.
– Restrict VM sizes: Define a policy that restricts the VM sizes that can be used within the Azure Landing Zone, ensuring alignment with cost optimization and performance requirements.
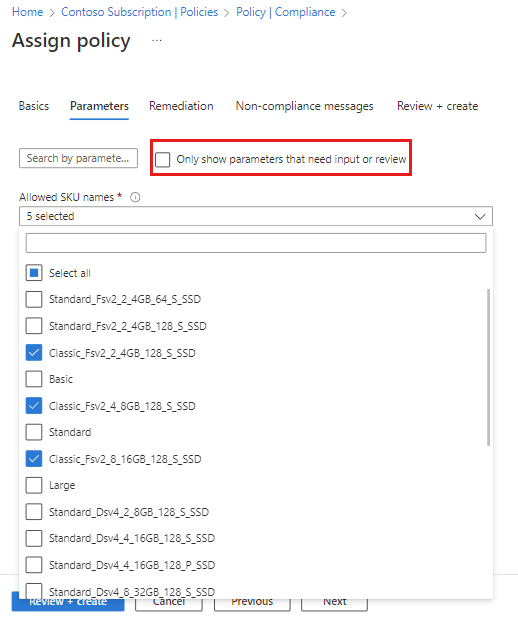
Source, How to restrict the virtual machine sizes
Enable Azure Security Center: Enforce the deployment and configuration of Azure Security Center to enable advanced threat protection, vulnerability assessments, and security recommendations.
4. Role Assignments:
Owner assignment: Assign the “Owner” role to specific individuals or groups responsible for managing the overall Azure Landing Zone. Better yet, use a privileged identity model (PIM) to allow temporary elevation for actions which require Owner permissions for specified tasks.
Contributor assignment: Assign the “Contributor” role to teams responsible for managing and deploying resources within the Landing Zone.
Read-only assignment: Assign the “Reader” role to auditors and compliance teams to provide visibility into resource configurations and activities.
5. Resource Groups:
Define resource group structure: Create separate resource groups for different environments (e.g., dev, test, prod) and business functions.
Apply naming conventions: Implement naming conventions for resource groups to ensure consistency and easy identification of resources.
6. Networking:
Define virtual network structure: Define the virtual network (VNet) hierarchy, including hub and spoke architecture for connectivity with on-premises networks.
Apply network security controls: Implement network security groups (NSGs) and firewall rules to control inbound and outbound traffic between resources and subnets.
Enable Azure Bastion: Deploy Azure Bastion for secure remote access to virtual machines through the Azure Portal.
7. Monitoring and Metrics:
Enable Azure Monitor: Configure Azure Monitor to collect and analyze resource-level metrics, enabling proactive monitoring of VM performance, storage usage, and network traffic.
Set up alerts and notifications: Define alert rules for critical events, such as high CPU utilization, network connectivity issues, or security breaches. Notify the appropriate stakeholders via email or Azure Monitor action groups.
8. Documentation and Compliance Reports:
Attach Compliance Reports: Include compliance reports, such as Azure Policy compliance reports and Azure Security Center findings, to demonstrate adherence to regulatory standards and security requirements.
Azure Bicep Deployments
Another method that can be adopted to deploy your Azure Landing Zone is using Bicep.
The ALZ team have an incredibly robust set of resources for planning and deploying using Bicep.
Below is the High-Level Deployment Flow for the Azure Landing Zone and associated modules:
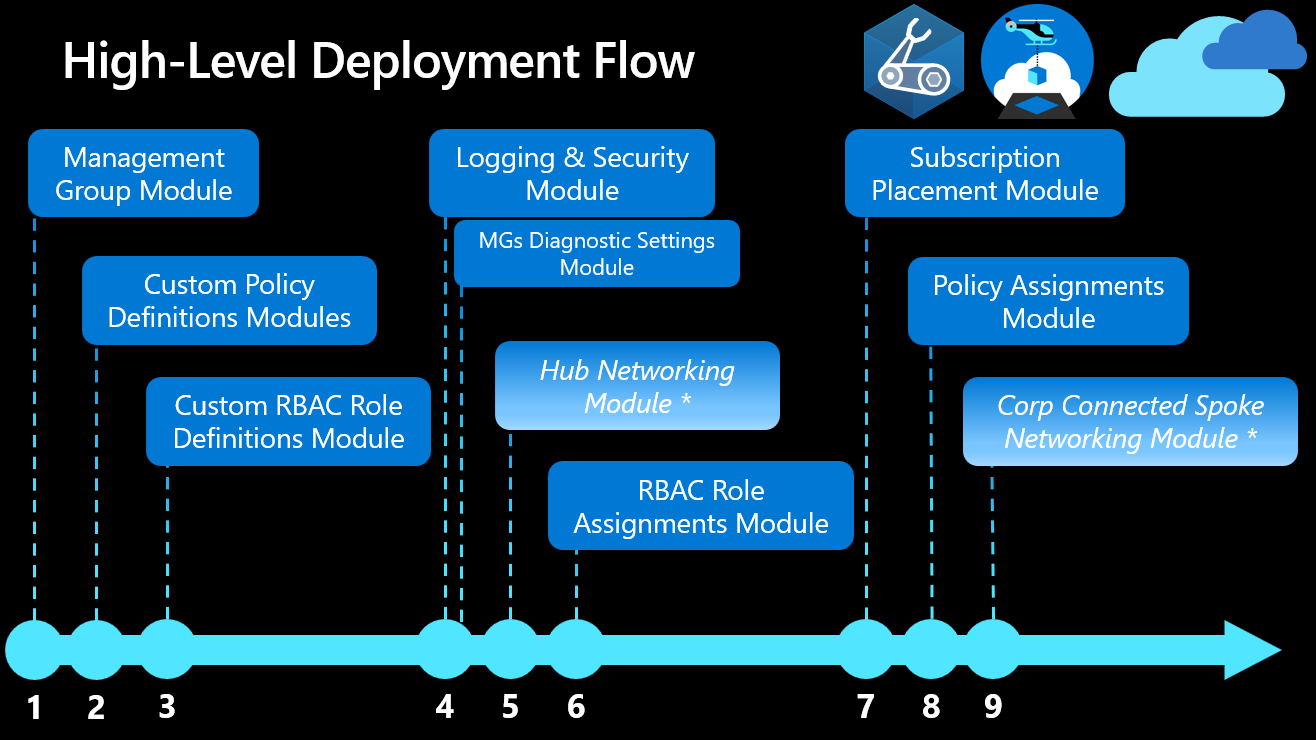
Azure Landing Zones Bicep – Deployment Flow
Conclusion
Chapter 2 of our blog series focused on the crucial elements of planning your Azure Landing Zone.
By carefully assessing organizational requirements and goals, understanding the Azure Resource Hierarchy and RBAC, defining deployment regions and networking considerations, and implementing Azure policies, blueprints, and governance frameworks, you can establish a solid foundation for your Azure environment.
Proper planning empowers you to design a scalable and secure infrastructure that aligns with your organization’s needs, optimizing performance, ensuring compliance, and enabling efficient resource management. In the next chapter, we will explore the process of designing the architecture of your Azure Landing Zone, providing insights on structuring subscriptions, network topology, and identity and access management.
Coming Soon!
Chapter 3: Designing Azure Landing Zone Architecture
- Introduction: Design principles for Azure Landing Zone
- Azure subscription structure and management groups
- Resource Group design and naming conventions
- Network Topology: Virtual Networks, Subnets, and Network Security Groups
- Identity and Access Management (Azure AD, RBAC)
- Greenfield & Brownfield Considerations
Thanks for reading!



