EXAMOLWelcome to the blog series:
Exploring Microsoft Azure Landing Zone Best Practices.
In this series, we will dive deep into the concept of the Azure Landing Zone and explore the best practices that organizations can follow to design, implement, and manage their Azure estate effectively.
Whether you are new to Azure or already have an existing Azure environment, this series will provide valuable insights and guidance to optimize your cloud journey using Azure Landing Zone.
Chapter 3:
Designing Your Azure Landing Zone
- Introduction: Design principles for your Azure Landing Zone
- Greenfield & Brownfield Considerations
- Azure subscription structure and management groups
- Resource Group design and naming conventions
- Network Topology: Virtual Networks, Subnets, and Network Security Groups
- Identity and Access Management (Azure AD, RBAC)
Introduction:
Design Principles for your Azure Landing Zone
Designing an Azure Landing Zone requires adherence to well-established design principles that ensure the architecture is scalable, secure, efficient, and reliable. The Microsoft Well Architected Framework (WAF) and Cloud Adoption Framework (CAF) provide valuable guidance and best practices for designing and implementing Azure Landing Zones.
This chapter explores the key design principles derived from these frameworks to help organizations build a robust Azure Landing Zone architecture.
1. Scalability:
Scalability is a critical design principle for an Azure Landing Zone, as it allows organizations to meet changing demands effectively.
The WAF suggests leveraging services like Azure Virtual Machine Scale Sets or Azure Kubernetes Service (AKS) to enable horizontal and vertical scaling of workloads. Additionally, CAF recommends employing Azure Resource Manager (ARM) templates to automate the provisioning and configuration of resources, thereby facilitating efficient scaling.
2. Security:
Security is a top priority in any Azure Landing Zone design. Both WAF and CAF emphasize the implementation of defense-in-depth strategies to protect resources and data. This includes employing Azure Identity and Access Management (IAM) controls, implementing RBAC, and enforcing Multi-Factor Authentication (MFA) for added security.
The use of Azure Security Center and Azure Sentinel helps organizations identify and respond to security threats actively. Encryption of data in transit and at rest using Azure Key Vault and Azure Storage Service Encryption is also recommended to ensure data security and compliance.
3. Efficiency:
Efficiency is vital to optimize resource usage and reduce costs within an Azure Landing Zone. WAF and CAF suggest utilizing Azure Cost Management and Azure Advisor to monitor and optimize resource consumption. Implementing automation through Azure DevOps, Infrastructure as Code (IaC), and Azure Automation can also help streamline deployment, management, and scale operations.
4. Reliability:
Reliability is essential for maintaining high availability and resilience of services and applications in the Azure Landing Zone. The WAF advocates implementing infrastructure redundancy and fault tolerance by leveraging Azure Availability Zones or Azure Availability Sets.
Deploying application components across multiple Azure regions using Azure Traffic Manager or Azure Front Door increases resilience during regional outages. Additionally, CAF emphasizes leveraging Azure Monitor and Azure Application Insights to proactively monitor and troubleshoot performance and availability issues.
5. Operational Excellence:
Operational excellence is achieved by applying best practices for managing and monitoring the Azure Landing Zone environment.
WAF and CAF suggest implementing comprehensive logging and monitoring solutions, such as Azure Monitor, Azure Log Analytics, and Azure Diagnostics, to gain insights into the performance, behavior, and health of resources.
Leveraging Azure Automation and Azure Policy enables organizations to automate common operational tasks, enforce policies, and ensure compliance with standards.
Greenfield & Brownfield Considerations
Consider this sample brownfield architecture below, notice the way in which services have been structured?
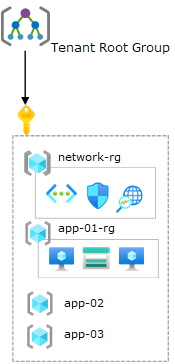
Source, Transition existing Azure environments to the Azure landing zone conceptual architecture
If we stop to compare this to the principles so far discussed throughout this series, a few observations can be made:
There is a single Azure subscription deployed with no custom management groups. A non-uniform resource distribution. Platform and workload resources are deployed in the same Azure subscription. Minimal usage of Azure Policy. Policy assignments (audit and deny effects) are done per resource group with exceptions. Resource groups are treated as units of management and scale.
RBAC role assignments per resource group containing a single VNet with no hybrid connectivity (VPN or ExpressRoute) but instead a new subnet is created per application. Multiple self-contained applications in each of the app-xx-rg resource groups. The platform architecture and it’s individual components are controlled and operated by different application or service teams.
Architectures such as this do not align with the principles of the The Microsoft Well Architected Framework (WAF) or the Cloud Adoption Framework (CAF).
If your current environment mimics this structure for your resources, start by working through the below design principles to better align your architecture.
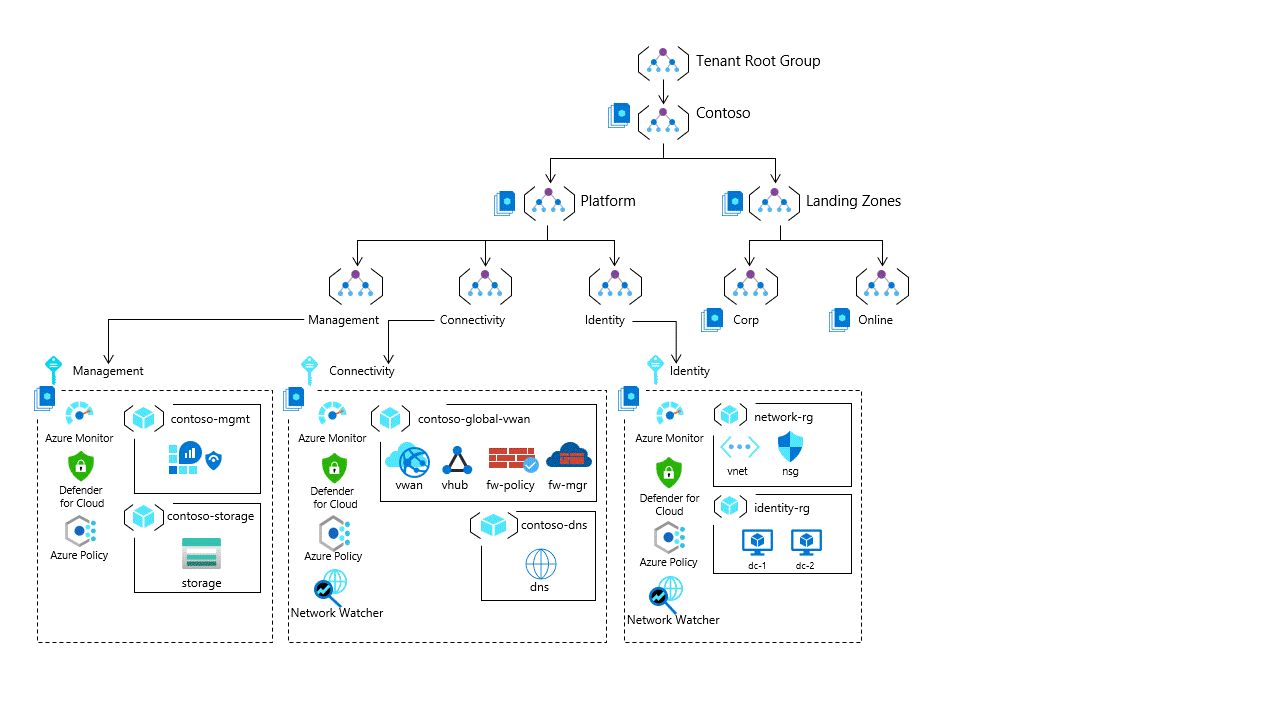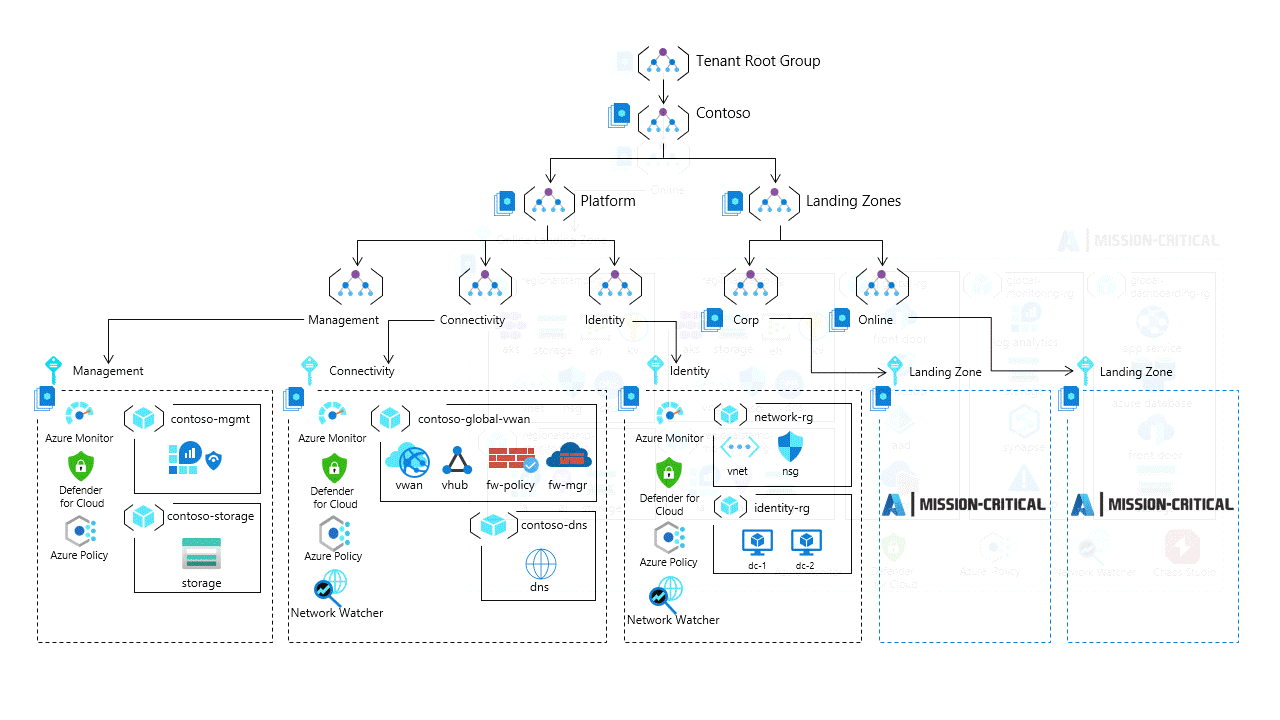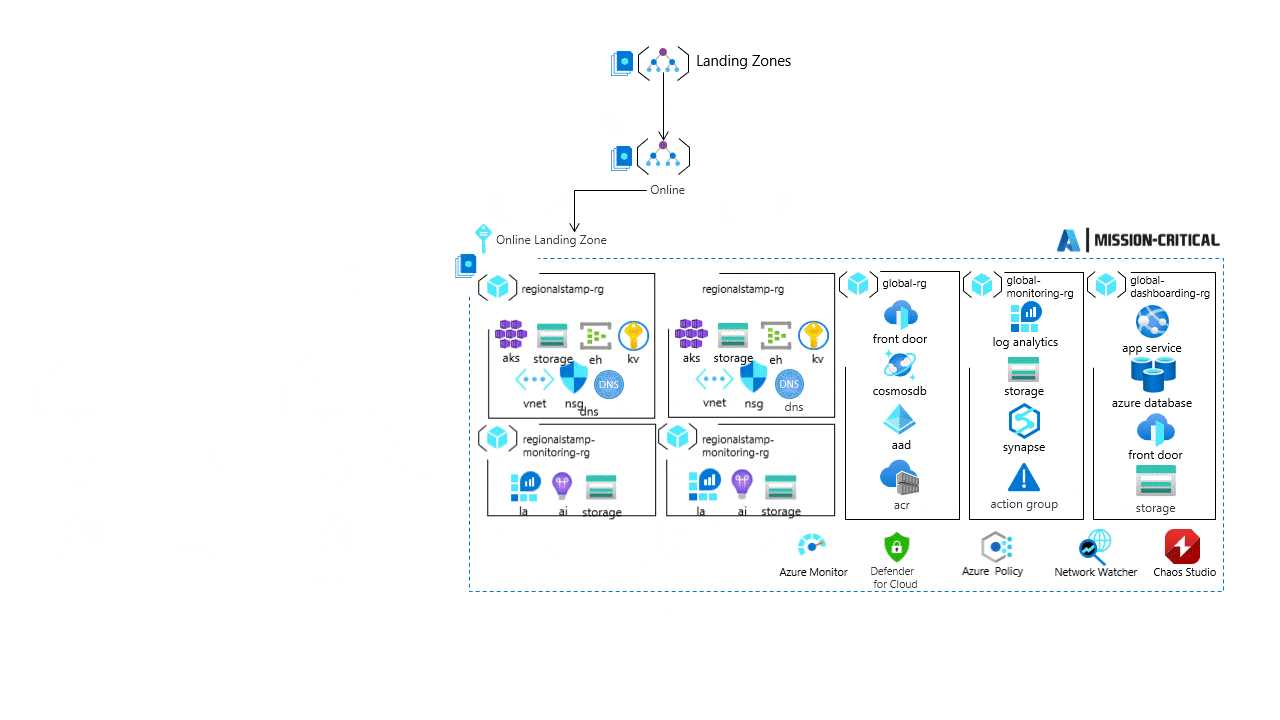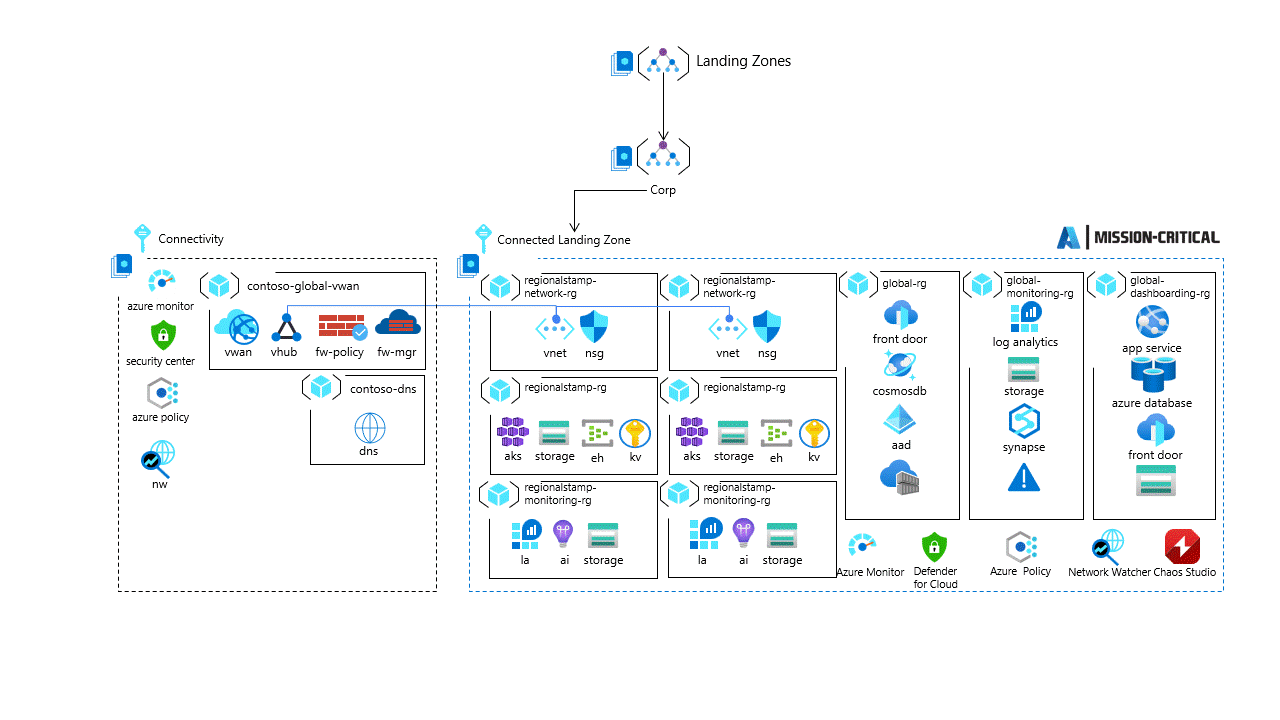
Resource Hierarchy and Subscription Structure
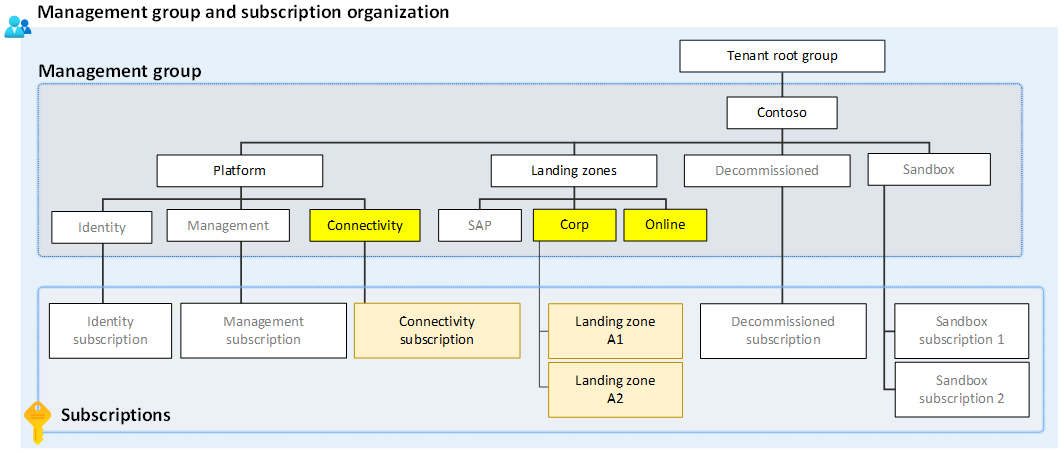
Source, Management Group & Subscription Structure
Establishing a well-structured resource hierarchy and subscription structure is a key aspect of designing a successful Azure Landing Zone architecture. This emphasizes the significance of following best practices derived from the Microsoft Well-Architected Framework to ensure scalability, efficient management, access control, and cost optimization within the Azure environment.
In the resource hierarchy, organizations utilize management groups, subscriptions, and resource groups to organize and manage their Azure resources effectively. The Well-Architected Framework recommends adopting a hierarchical approach to gain better control and governance over resources at scale.
Management groups serve as containers for organizing and applying policies at scale. They allow organizations to group subscriptions based on common attributes, governance requirements, or security boundaries. This enables consistent policy enforcement and simplifies organizational management.
For example, an organization might create management groups based on business units or departments.
Naming Standards are just as critical when deploying resources within the Landing Zone, some examples and best practice suggestions:
The following table shows restrictions and naming patterns for resource groups, availability sets, and tags.
| Resource group | Availability set | Tag | |
|---|---|---|---|
| Scope | Subscription | Resource group | Associated entity |
| Length | 1-90 | 1-80 | 512 (name), 256 (value) |
| Valid characters | Alphanumeric, underscore, parentheses, hyphen, and period except at end | Alphanumeric, underscore, and hyphen | Alphanumeric, spaces, and Unicode characters except for angle brackets, percent symbol, ampersand, forward or back slashes, question mark, or period |
| Suggested pattern | <service-short-name>-<environment>-rg |
<service-short-name>-<context>-as |
key : value |
| Example | profx-prod-rg |
profx-SQL-as |
Department : Central IT ☺ |
Source, Organize your Azure resources effectively
Subscriptions act as isolated instances of Azure that provide a logical and billing boundary for resources. They enable organizations to have better control over access management, billing, and resource usage.
The Well-Architected Framework suggests a structured subscription model aligned with business functions, projects, or environments. This allows teams to have autonomy within their subscription while adhering to overarching governance policies.
Resource groups are logical containers within a subscription that help organize, manage, and secure resources. They act as a unit for deployment, access control, and cost management.
By grouping resources based on business functions, teams, or applications, administrators can apply security policies, implement consistent tagging, and streamline resource management.
The flexibility of resource groups allows for efficient provision, update, and deletion of resources within a scoped boundary.
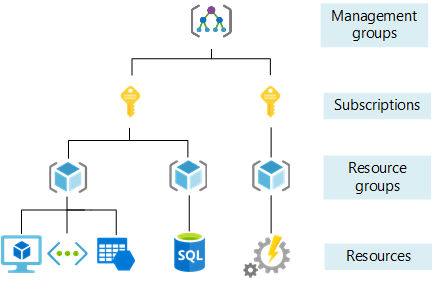
Source, Organize your Azure resources effectively
When designing the subscription structure within the Azure Landing Zone, it is crucial to consider scalability and resource limits.
Azure has certain limits on the number of subscriptions per Azure AD tenant, Azure Resource Manager quotas, and subscription-based quotas on resource types. Adhering to these limits and quotas ensures smooth scaling of the Azure environment and prevents potential limitations.
Before deploying subscriptions, take a look at the resource limits per deployment within the Azure subscription and service limits, quotas, and constraints.
For example, a large organization operating in multiple regions might structure its Azure Landing Zone with management groups representing regional divisions or business units. Within each management group, subscriptions can be created based on specific projects or environments. Resource groups can then be organized based on application tiers or individual services within each subscription.
This hierarchical structure allows for clear visibility, effective governance, and efficient management of resources while enabling scalability and ease of administration.
The following landing zone archetype examples may help you to understand their purpose and intended use:
| Landing zone archetype (management group) | Purpose or use |
|---|---|
| Corp | The dedicated management group for corporate landing zones. This group is for workloads that require connectivity or hybrid connectivity with the corporate network via the hub in the connectivity subscription. |
| Online | The dedicated management group for online landing zones. This group is for workloads that might require direct internet inbound/outbound connectivity or for workloads that might not require a virtual network. |
| Sandbox | The dedicated management group for subscriptions that will only be used for testing and exploration by an organization. These subscriptions will be securely disconnected from the corporate and online landing zones. Sandboxes also have a less restrictive set of policies assigned to enable testing, exploration, and configuration of Azure services. |
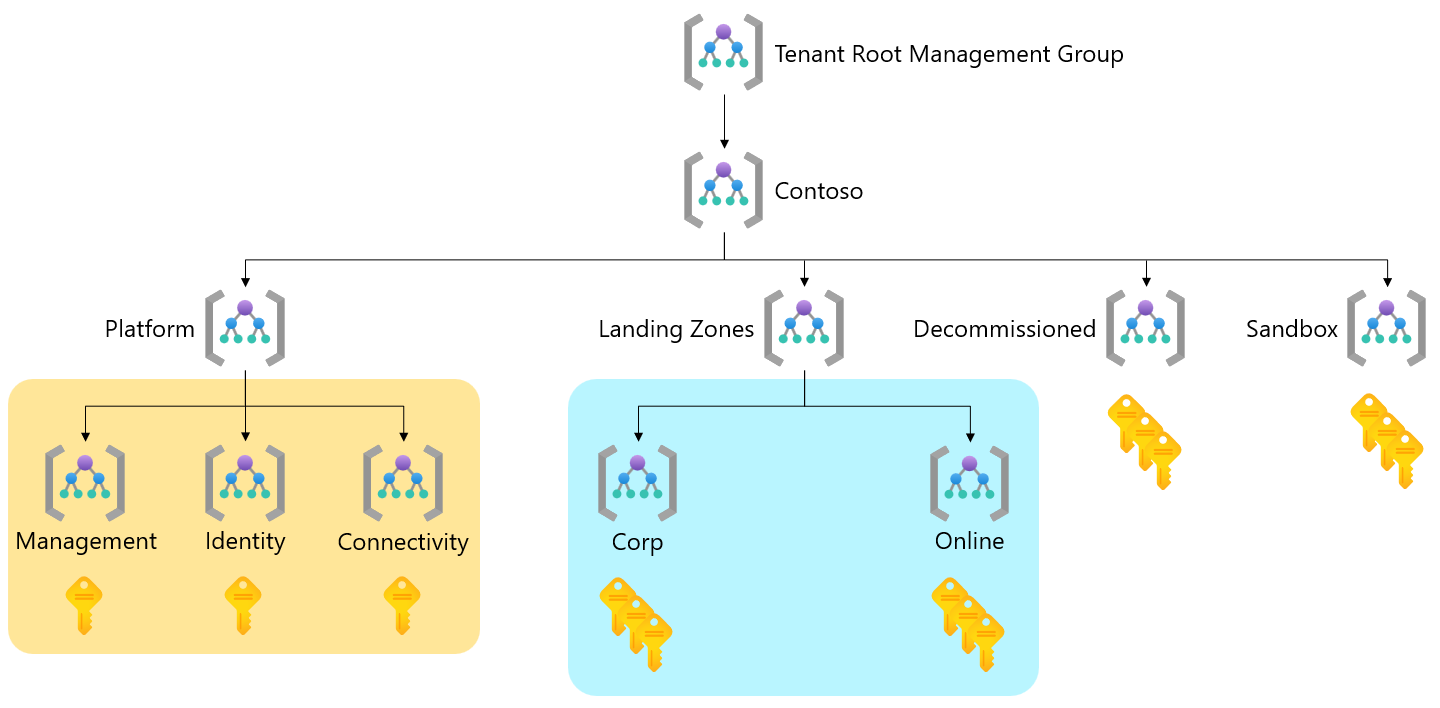
Source, Tailor the Azure landing zone architecture to meet requirements
Identity and Access Management (IAM)
Identity and Access Management (IAM) is a critical aspect of designing an Azure Landing Zone architecture, ensuring secure and controlled access to Azure resources. This subtopic delves into the importance of effective IAM practices, the role of Azure Active Directory (Azure AD), and the implementation of Role-Based Access Control (RBAC) within the Azure Landing Zone architecture.
IAM is fundamental to establish proper authentication, authorization, and accountability in the Azure environment. It enables organizations to manage user identities, control access to resources, and enforce security policies. By implementing IAM practices, organizations can ensure that only authorized individuals have the appropriate access levels based on their roles and responsibilities.
Role-Based Access Control (RBAC) is a fundamental component of IAM in Azure. It provides fine-grained access control by assigning roles to users, groups, or security principals. Azure provides a set of built-in roles with predefined permissions, such as owner, contributor, and reader. These roles can be assigned at different levels, including management groups, subscriptions, and resource groups, allowing for granular control over resource access.
When planning IAM for the Azure Landing Zone architecture, organizations should follow the principle of least privilege. This principle ensures that users have the minimum permissions necessary to perform their designated tasks. By assigning roles based on job functions, organizations can reduce the risk of unauthorized access, accidental misconfigurations, and potential security breaches.
Azure AD offers additional features like Conditional Access and Azure AD Privileged Identity Management (PIM). Conditional Access allows organizations to define policies for accessing resources based on specific conditions such as location, device compliance, or risk factors.
This further enhances the security of the Azure Landing Zone by allowing organizations to adopt a risk-based approach to access management. Extending a security framework which follows Zero Trust principles.
Azure AD Privileged Identity Management (PIM) provides just-in-time access to elevated permissions, reducing the overall exposure of privileged accounts. PIM allows organizations to assign time-bound access to specific roles, allowing users to activate these roles only when needed. This helps mitigate the risks associated with long-term elevated access.
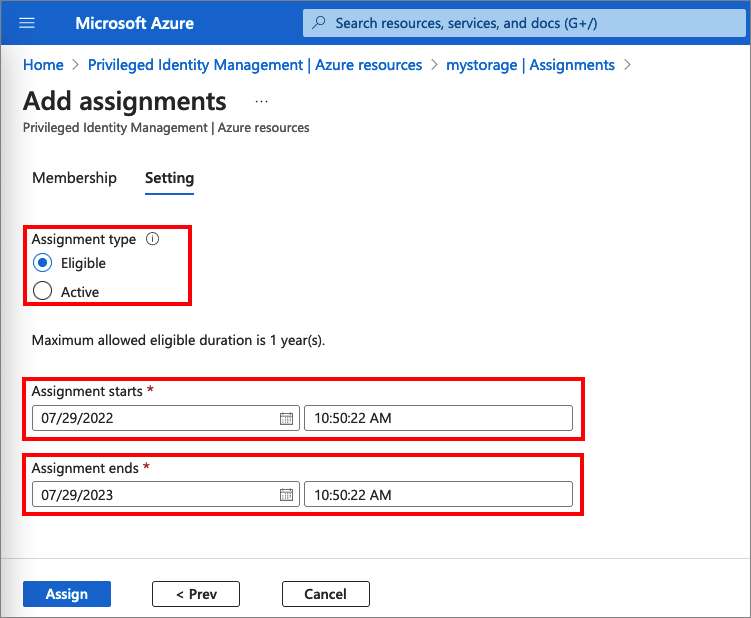
Source, The screenshot shows how administrator assigns a role to members.
Implementing IAM in the Azure Landing Zone architecture ensures proper access control and accountability. It allows organizations to manage identities effectively, enforce authentication policies, and control resource permissions. By leveraging Azure AD, RBAC, Conditional Access, and Azure AD PIM, organizations can establish a secure and manageable IAM framework within their Azure environment.
Designing an effective network topology is vital for achieving a secure and well-connected Azure Landing Zone. This subtopic delves into the considerations related to network design, subnet configurations, and the implementation of network security groups (NSGs) for enforcing network security measures.
Network Topology, Subnets, and Network Security Groups
When establishing an Azure Landing Zone, it is important to carefully plan the network topology. This involves designing the structure of virtual networks (VNets) and subnet configurations to support the desired level of connectivity and isolation.
A well-designed network topology should reflect the organization’s requirements for secure and efficient communication between different resources and environments within the Azure environment.
Microsoft provide useful tools in viewing your current assets with regard to your network infrastructure, for details check out the new Topology experience which offers visualization of Azure resources for ease of inventory management and monitoring network at scale. Leverage it to visualize resources and their dependencies across subscriptions, regions and locations.
The use of virtual network peering allows organizations to connect VNets seamlessly, enabling secure and private communication between them. Peering VNets can be a beneficial approach to simplify network architecture and facilitate resource sharing across multiple VNets.
Subnets play a crucial role in segmenting the virtual network into smaller address spaces, enhancing security by isolating resources and controlling traffic flow. By appropriately dividing the VNet into subnets based on workload types or security requirements, organizations can apply more granular network security measures and implement network virtual appliances for routing and filtering traffic.
When designing subnets, organizations should consider factors such as scalability, network performance, and resource requirements. By carefully planning subnet sizes and IP address ranges, administrators can efficiently utilize address space and ensure sufficient capacity for future growth.
Network Security Groups NSGs are an integral part of network security in Azure. They allow organizations to enforce network traffic filtering rules at the subnet and network interface level. NSGs work in conjunction with Azure’s built-in distributed denial-of-service (DDoS) protection, virtual network service endpoints, and other security features to provide defense-in-depth for the Azure Landing Zone.
NSGs can be configured to allow or deny inbound and outbound traffic based on criteria such as source/destination IP addresses, ports, and protocols.
By defining specific rules in NSGs, organizations can control communication between subnets, restrict access to resources, and minimize the attack surface. To enhance network security, NSGs can be associated with individual subnets, network interfaces, or even applied at the entire VNet level. This flexibility enables fine-grained control over network traffic and strengthens overall security posture.
It is important to note that the careful design and management of NSGs are crucial for strike a balance between security and operability. Organizations should regularly review and update NSG rules to align with changing security requirements and business needs.
In conclusion, a well-designed network topology, proper subnet configurations, and effective utilization of NSGs are essential components of building a secure Azure Landing Zone. Planning the network structure, segmenting the VNet into subnets, and using NSGs to enforce appropriate traffic filtering rules are vital for achieving network security, isolation, and control. By carefully considering these aspects, organizations can establish a resilient and secure network foundation for their Azure resources and workloads.
Conclusion
In this chapter we covered high-level design principles and concepts for readers who are looking to start their journey in assessing Azure Landing Zone design concepts.
For mission critical workloads, see the Mission-critical baseline architecture in an Azure landing zone for a deeper dive with prescriptive architectural approach to building highly-reliable cloud-native applications on Microsoft Azure for mission-critical workloads.
Thank you for reading!



